VPN Filter: malware attacks router and NAS systems

Over 500,000 routers and NAS systems in 54+ countries are now infected with new malware. The malware named “VPN Filter” is highly destructive and in the worst case can even destroy the infected device.
(Please also read our updated article here with a list of affected devices)
The US-American IT security company Talos, a subsidiary of the well-known router manufacturer Cisco, warns of a huge bot-network whose creators are deliberately attacking routers and NAS systems (network storage devices) on the Internet of Things. Talos claims that it has already identified over 500,000 infected devices.
Currently, the main devices affected are Netgear, TP-Link, Linksys and Mikrotik, which are primarily used by private users, the self-employed and small companies. The malware is also said to have infected NAS devices from the manufacturer QNAP. Symantec has compiled a list of all previously identified vulnerable devices:
https://www.symantec.com/blogs/threat-intelligence/vpnfilter-iot-malware
According to Cisco Talos, the notorious hacker group “Fancy Bear” is said to be responsible for the malware attack, which in the past was already blamed for various attacks in the USA and Western Europe.
Cisco Talos suspects state actors behind VPN Filter and suggests in the context a responsibility of the Russian government – or the Russian secret service. Cisco Talos points to a characteristic error in the implementation of the RC4 encryption used, which had already been noticed with the malware “BlackEnergy”. Specialists of the US Department of Homeland Security also suspect their origins among “state actors” of the Russian government apparatus.
The fact that security researchers have now become aware of the malware is due to an increase in infections in recent weeks. Especially devices in the Ukraine are currently the target of attacks – this is also seen as a further indication of a major attack controlled by Russia. On Wednesday evening, the FBI confiscated a Russian bot server that was supposedly used to control the infected routers.
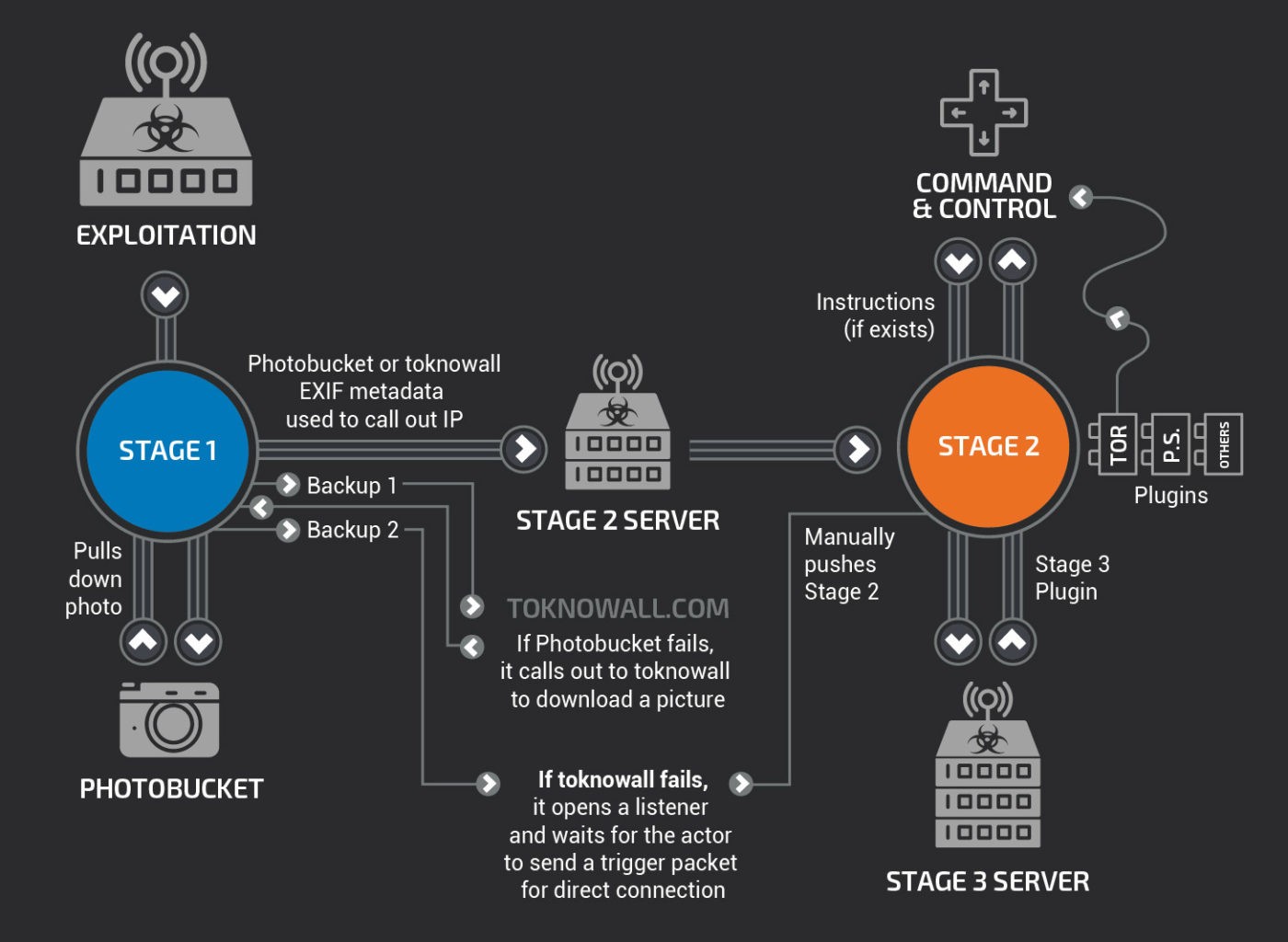
The malware itself works according to a well-known procedure. At first, smaller software nests itself on compromised devices. This allows access to the device – and can download additional software or code via the Internet upon instruction/automatically. The actual purpose – the actual task – of the malware is still suspected. VPN Filter uses the TOR network and other proxy/relay servers – but it has not yet been established what for.
One particularly worrying feature of VPN Filter, however, is that the malware has a feature that can render the infected device unusable upon instruction. VPN Filter then overwrites the first 5000 bytes of the first block device (/dev/mtdblock0), which causes it to stop starting. This enables the operators of the bot-network to carry out “a destructive attack on a large scale”.
According to Cisco Talos, Symantec and Co., there is currently only one effective measure for owners of infected devices: resetting the devices to the factory settings.
The release of firmware updates/security patches by the manufacturers of vulnerable devices still needs to be waited for.