Torii: Evolution of IoT Malware

In recent months, the well-known IoT malwares, cryptominers and botnets such as Mirai, Qbot and Gandcrab (etc.) have often caused trouble, worries and economic damage. The antivirus specialist Avast now warns of a new, progressive threat: Torii.
Avast has conducted an initial in-depth analysis of the new threat. The maliciousness of Torii seems enormous; the possibilities of the malware exceed the potentials of the IoT Malwares known so far.
Caught red handed
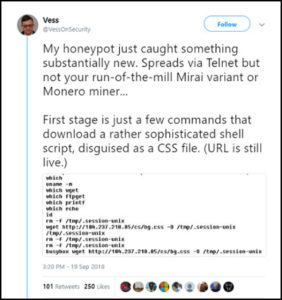
Torii was first discovered by the Bulgarian antivirus and security expert Vesselin Bontchev (https://twitter.com/vessonsecurity), who runs a Telnet Honeypot server on the Internet (of Things) – and thereupon published a warning and part of the source code of the malware on Twitter.
Torii (or its host server) searches the Internet of Things for open – or only secured with default passwords – Telnet access on servers and devices.
(Telnet is a protocol used on the Internet or local area network to provide a bidirectional interactive text-oriented communication facility using a virtual terminal connection. User data is interspersed in-band with Telnet control information in an 8-bit byte oriented data connection over the Transmission Control Protocol (TCP). Telnet was developed in 1969 beginning with RFC 15, extended in RFC 855, and standardized as Internet Engineering Task Force (IETF) Internet Standard STD 8, one of the first Internet standards. The name stands for “teletype network”. – Source: Wikipedia)
If Torii can successfully establish itself on an insufficiently secured device via Telnet, it performs an analysis of the infected device and then connects to its Command and Control (CnC). Torii first transmits information to the CNC server, including the system and processor architecture of the newly infected host, and then loads additional architecture-specific code.
TOR – Anonymization Service as Name Giver
The malware communicates with its CnC servers via the anonymization network of Tor servers, so Avast analysts named the malware “Torii”.
(Tor is free software for enabling anonymous communication. The name is derived from an acronym for the original software project name “The Onion Router”. Tor directs Internet traffic through a free, worldwide, volunteer overlay network consisting of more than seven thousand relays to conceal a user’s location and usage from anyone conducting network surveillance or traffic analysis. Using Tor makes it more difficult to trace Internet activity to the user: this includes “visits to Web sites, online posts, instant messages, and other communication forms”. Tor’s intended use is to protect the personal privacy of its users, as well as their freedom and ability to conduct confidential communication by keeping their Internet activities from being monitored. – Source: Wikipedia)
Currently, Torii “supports” devices under arm, x86, x64, Motorola 68k, MIPS, PowerPC and SuperH.
Although the Avast investigation continues, it’s clear that Torii is an example of the development of IoT malware and that its sophistication is well above what we’ve seen so far.
Once it infects a device, it not only sends a whole bunch of information about the computer/device on which it resides to the CnC, but also allows the Torii operators, by communicating with the CnC, to execute arbitrary code or deliver any payload to the infected device.
This suggests that Torii could become a modular platform for future use. Since the payload itself does not look for other potential targets, it is relatively unobtrusive on the network layer as well.
Until there are appropriate defense and cleaning options against the new threat, you can still protect yourself and your IoT infrastructure best by beeing cautious!
Standard passwords should be changed immediately when commissioning a new device – or after updating a firmware. If you do not use Telnet for communication in your network/devices, you can turn off the service.
Additional – although probably only temporary – protection is provided by blocking connections to the domains currently used by Torii.
Known are:
- top.haletteompson.com
- cloud.tillywirtz.com
- trade.andrewabendroth.com
(All under IP 66.85.157.90)
Other domains registered on the Command and Control IP that could possibly be used in the future:
- cloud.tillywirtz.com
- dushe.cc
- editor.akotae.com
- press.eonhep.com
- web.reeglais.com
- psoriasiafreelife.win
- q3x1u.psoriasiafreelife.win
- server.blurayburnersoftware.com
- top.haletteompson.com
- trade.andrewabendroth.com
- www.bubo.ccwww.dushe.cc
Torii attempts to resolve the IPs of its CnC servers via the public Google DNS (8.8.8.8). If you use your provider’s DNS servers anyway, you could also add the IP of the Google DNS to the list of connections to be blocked.
As mentioned above, the new malware is not currently trying to perform any further activities after successfully infiltrating a device. A hijacked device will (currently) not execute scans or further code – but is remarkably protected against device restarts and cleanup attempts and uses up to 6 different ways to retry to restart itself after a device reset.