Poor IoT security, expensive pleasure
On September 21, 2016, I(o)T security analyst Brian Krebs’s website became the target of a huge, extraordinary DDoS (Distributed Denial of Service) attack – possible only through poor IoT security – and a resourceful hacker.
The attack began on the evening of the 21st at about 8 pm. With up to 665 gigabits per second (!), a huge network of hacked and Miari-infected Internet of Things (IoT) devices such as Internet routers, security cameras and digital video recorders hammered onto the analyst’s server, whose infrastructure was protected by Akamai’s DDoS protection. Read also: The IoT under attack: Was Mirai just the beginning?
According to Akamai, the volume of the attack on Brian Krebs website was almost twice as large as the largest attack they had seen before – and was also one of the largest DDoS (Distributed Denial of Service) attacks the Internet has ever experienced.
A new study attempting to measure the direct cost of this one attack for IoT device users whose machines and devices were used for the attack found that it could have cost device owners a total of $323,973.75 in excess power and additional bandwidth consumption.
By 2016, when the attack described above took place, the hacker behind Miari had taken control of over 600,000+ devices – poor IoT security made it possible. For the attack on Brian Krebs blog, however, only about 24,000 devices were used – a twenty-fifth (1/25) of the potential available at that time.
A DDoS attack of 600,000 enslaved IoT devices at ~16+ terabits per second would probably paralyze even military digital infrastructures – at a cost of several million by the attack itself.
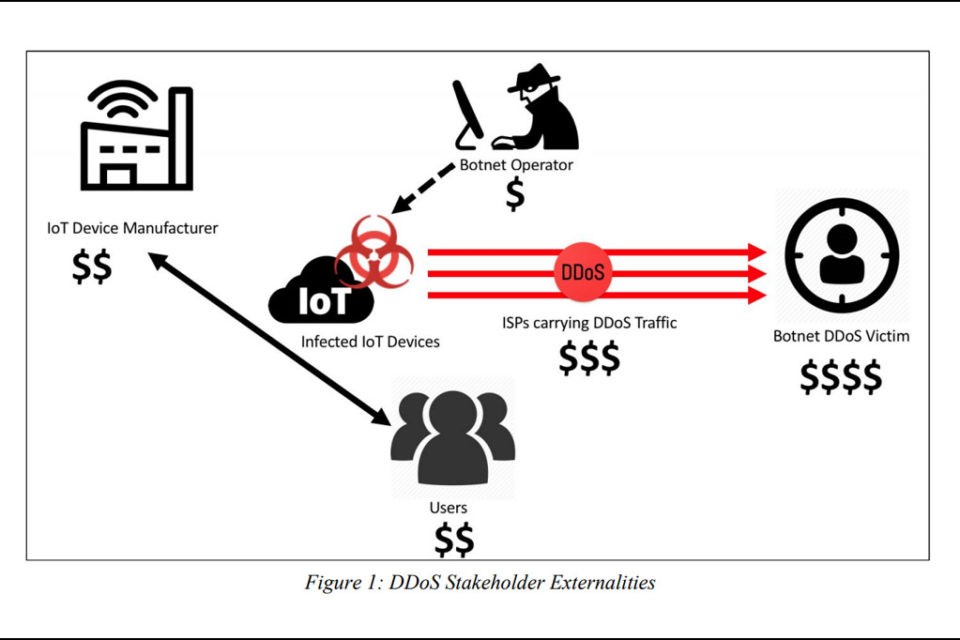
Future attacks of this kind will continue to have the same cause as in 2016, blamed (and will be blamed) on IoT device manufacturers for marketing cheap, badly designed products (by default unsafe) – but blamed also on customers who buy these IoT devices and connect them to the Internet without even having changed the factory settings of the devices (usually the default passwords).
Following a recent report, over 7.5 million DDoS attacks were registered in 2017, many of them on commercial/commercial providers. Of these, over 55% suffered financial losses of between $10,000 and $100,000 as a result of these attacks. This damage has almost doubled compared to the previous year.