Let’s talk about the key to IoT security

The Internet of Things might not be spreading as quickly as predicted by some, but in the long run it will change our world significantly. As more IoT devices enter the market, security will become increasingly important.
In his new ebook “Making sense of IoT”, Kevin Ashton who shaped the term ‘Internet of Things’ defines IoT as follows:
The ‘Internet of Things’ means sensors connected to the Internet and behaving in an Internet-like way by making open, ad hoc connections, sharing data freely and allowing unexpected applications, so computers can understand the world around them and become humanity’s nervous system.
While free data sharing and smart computers, that understand the world better and enrich and make our lives easier, are certainly desirable things, we all know that the nervous system is also an extremely vulnerable thing. And in the world of bits and bytes, the greatest of its flaws is security. According to the new Aruba study, “The Internet of Things: Today and Tomorrow”, more than 50% of the participants think that external attacks are the biggest problem for IoT. So, it seems that making IoT devices safer, to prevent data theft and manipulation as well as the hijacking of devices into botnets, is a crucial task for all organizations dealing with IoT.
At Lemonbeat GmbH, our focus is on robust radio communication in the sub GHz RF band with devices that are sometimes battery-powered and without hardware crypto support. Nonetheless, these constrained devices are directly accessible via IPv6, so security is an important subject for us too.
So how do we face this challenge?
We deal with the challenge through a combination of two proven encryption systems — on the one hand the asymmetric RSA (named after its inventors Rivest, Shamir and Adlerman) and on the other the AES (Advanced Encryption Standard) encryption mechanism, a specification established by the U.S. National Institute of Standards and Technology in 2001.
By assessing and then weighing up the risk of vulnerability against the cost of security measures, we try to offer our customers in each case the proper solution, depending on their different demands. Henceforward this can range from deploying a suitable RSA method to the use of asymmetric Elliptic Curve Cryptography (ECC) that requires a far smaller key to provide the same security as RSA and the like. Furthermore, instead of common AES-128 we can use the more secure AES-256 that is even accepted and used by the U.S. government.
And what do we do in detail for security?
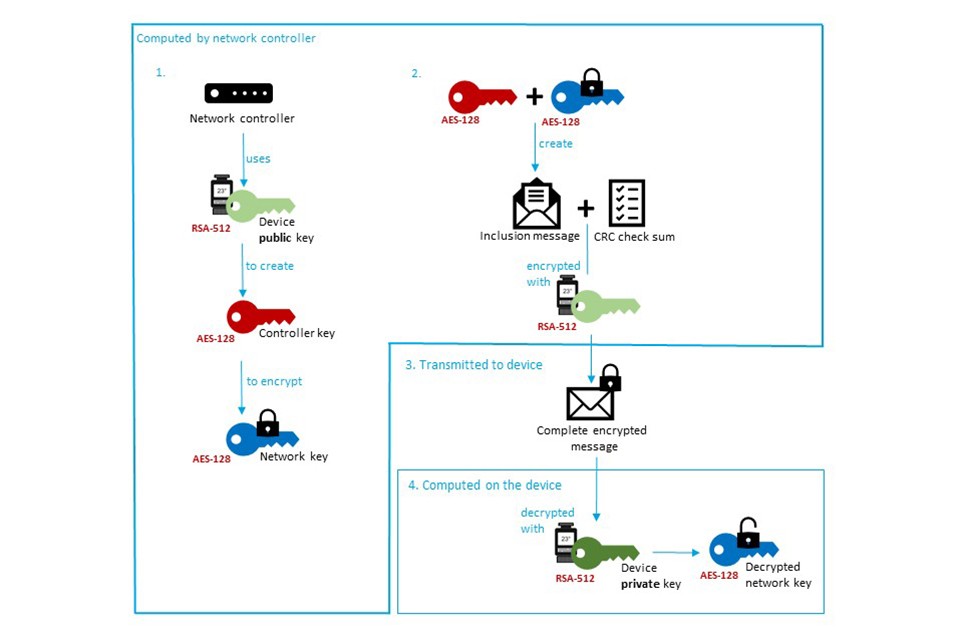
All Lemonbeat devices must be included into a Lemonbeat network. This ensures a secure communication with and between the devices as well as a tamper-proof configuration of the devices. Inclusion is done by exchanging keys. To increase the security here, we do not use a common key for all devices, as is often the case, but an individual key pair for each Lemonbeat device. While including a Lemonbeat device, the public RSA key of the device is saved in a backend. The network controller — responsible for managing our 868 MHz network — retrieves it from there. But this is only possible if the controller has already been paired with the backend in a secure manner.
After receiving the public key, the network controller generates a new unique AES key, the so called “controller key” that is used to encrypt the network key. Controller key and encrypted network key are then used to create an inclusion message. In addition, the network controller adds a check sum, generated with the CRC (Cyclic Redundancy Check) algorithm that will detect any transmission errors caused, for example, by radio interference, channel access collisions or a weak receive signal. The complete inclusion message is then encrypted with the public RSA key of the device. Only the device itself has the related private RSA key and can decrypt the message and therefore receive the decrypted network key. This network key is crucial for the device to device interaction because — due to limited processing power and battery capacity — constrained devices are usually not capable of generating a new key for each connection.
After the inclusion, all data transmitted via radio in the 868 MHz network is encrypted using the AES encryption system in combination with a counter mode like the CCM mode (Counter with CBC-MAC), that offers authentication as well as confidentiality. We use counter modes on different levels to prevent “replay attacks”, also known as “playback attacks”, where transgressors try to bypass protection measures by intercepting and resending valid messages and thus, trying to manipulate alarm or keyless entry system and so on.
Don’t get us wrong, security is an ongoing fight, and methods will continue to become more advanced, but all the combined methods mentioned above do not just sound a bit complicated, they really do ensure considerable security. As you can see, we try to give trespassers a really hard time. And the best bit is: It’s all part of the deal, so our customers don’t have to trouble themselves with creating their own methods to deal with the problem.