Honeypots “collected” five million attacks in thirty days
To conduct a study on data security in the cloud, UK IT security firm Sophos set up ten so-called honeypots and distributed them around the world to locations with high I(o)T activity.
(“In computer terminology, a honeypot is a computer security mechanism set to detect, deflect, or, in some manner, counteract attempts at unauthorized use of information systems. Generally, a honeypot consists of data (for example, in a network site) that appears to be a legitimate part of the site, but is actually isolated and monitored, and that seems to contain information or a resource of value to attackers, who are then blocked. This is similar to police sting operations, colloquially known as “baiting,” a suspect.” – Source: Wikipedia)
The cloud: an elementary component of modern IT; enables location-independent data access, increases cost efficiency, simplifies business processes, increases added value for consumers and much more. More and more companies and consumers are storing their data in the cloud. Protecting this data from access by cybercriminals is therefore a fundamental concern for IT security.
Cyberattacks on Honeypots
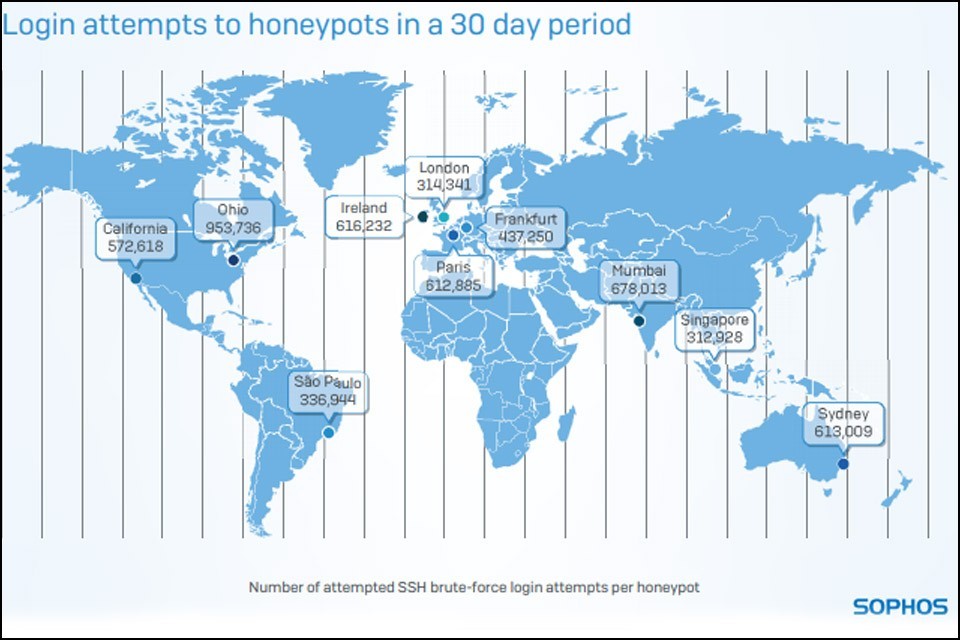
Sophos wanted to know how much cloud servers are exposed to potential hacker attacks, and has published this in a 30-day study entitled “Exposed: Cyberattacks on Cloud Honeypots” on the basis of ten honeypots.
(“Sophos Group plc is a British security software and hardware company. Sophos develops products for communication endpoint, encryption, network security, email security, mobile security and unified threat management. Sophos is primarily focused on providing security software to the mid market and pragmatic enterprise from 100- to 5,000-seat organizations. Whilst not a primary focus, Sophos also protects home users, through free antivirus software (Sophos Home) intended to demonstrate product functionality. It is listed on the London Stock Exchange and is a constituent of the FTSE 250 Index.” – Source: Wikipedia)
To this end, cloud honeypots have been set up in ten of the world’s most popular Amazon Web Services (AWS) data centers in Frankfurt, Ireland, California, London, Mumbai, Ohio, Paris, Sao Paolo, Singapore and Sidney, and it takes an average of only 40 minutes for a first attack on one of the honeypots! During the 30-day study, each honeypot was attacked an average of 13 times per minute – Frankfurt alone was the target of over 440,000 cyber attacks during the study period, but the time it took for the first of the honeypots to be attacked was almost record-breaking.
Only 52 seconds after the “decoy” was activated in Sao Paolo, Brazil, it was attacked. Paris and Sydney were 17 and 18 minutes online, respectively, until a first attack, Frankfurt an hour later, and Ireland a good 100 minutes, the longest until a first attack attempt.
Sophos Honeypots simulated a Secure Shell (SSH) service to measure SSH logon attempts. SSH is a remote access service used not only on commercial servers, but also by home users in home environments on devices such as webcams or NAS devices. On these systems, authorized users can connect via SSH to remotely configure the device or access files. However, once an attacker has left the login prompt on an IoT device behind, not only does an attacker gain the same access rights as the owner, but he often even gains administrative access to the attacked device.
Evaluating the findings during the test period again demonstrates that devices that did not receive the required reconfiguration after deployment (including changing factory installed default passwords on many devices) allow a hacker relatively easy access to these devices. The hackers are also speculating that factory configurations will not be changed – they used standard user names and popular, frequently used weak passwords in most logon attempts. The 123456 series, for example, was the most commonly used password for a logon attempt worldwide.
Like Kaspersky, Trend Micro and other IT security companies, Sophos makes recommendations for more secure operation of IoT devices and servers that users should be aware of:
- Change the passwords in the settings.
- Use a complex and unique password for each service.
- If necessary, use a password manager to manage the passwords, so that you only need to remember the master password (long and complex! Use numbers, special characters and spaces) of the manager.
- Turn off Universal Plug and Play on your router.
- On SSH servers, use key-based authentication, not just a password.
- Use fail2ban on Linux servers to limit the number of logon attempts.
- Use a powerful Linux AV solution, such as Sophos Antivirus for Linux.
- Use an AI-based cloud security solution with compliance automation, such as Sophos Cloud Optix, which uses AI to evaluate and reduce the threat risk of different cloud environments.
Alternatively, it is recommended that you use more sophisticated, secure solutions from the outset. Lemonbeat GmbH of Dortmund, Germany, for example, offers a conclusive security concept for its products that offers a very high level of security using two encryption methods combined with an authentication process at hardware level. It would be desirable if other manufacturers and publishers would in future also treat the data security of their customers and partners with such care.
The complete study in English as well as further information can be found at the following URLs:
Exposed: Cyberattacks on Cloud Honeypots
Lemonbeat GmbH
Let’s talk about the key to IoT security