HoneyBot: the IoT Honeypot
IT security is one of the most important factors especially in the Internet of Things – if compromised, it can pose a threat to global trade, the private sphere or even the basic infrastructure of modern society.
Internet security experts have been using bait computer systems (so-called “honeypots“) for some time to defend themselves against virtual attackers.
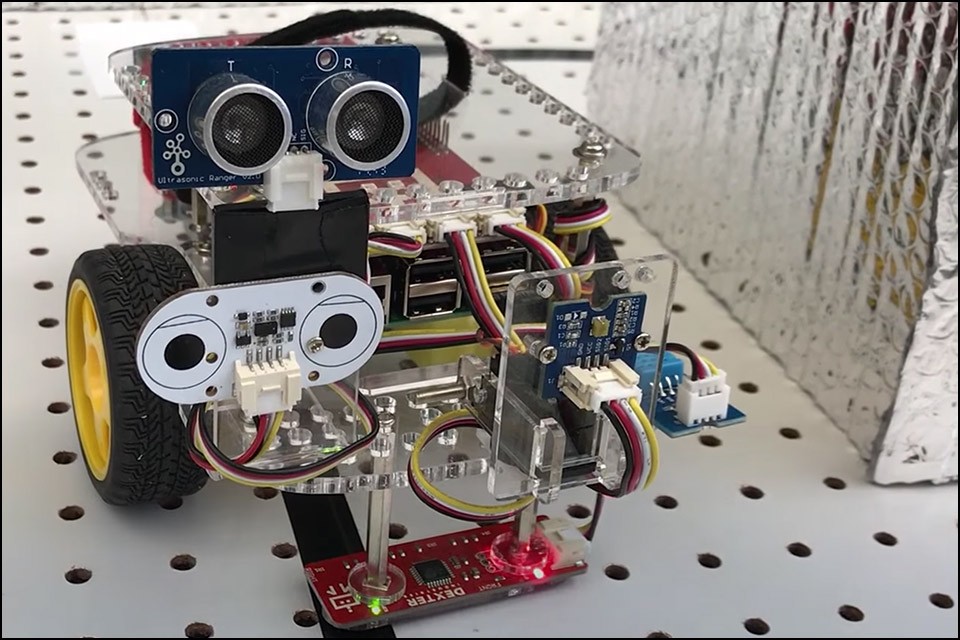
Last week, researchers at Georgia Tech’s School of Electrical and Computer Engineering presented a new interpretation of a modern honeypot: the HoneyBot robot. A kind of canary in the digital coal mine that provides an early warning when an attacker tries to penetrate an organization’s/household’s systems.
This “bait robot” occupies a security gap in the IoT, in which more and more devices can be found that were never designed for operation on the Internet/a networked environment – that go online both in private households and in factories and offer potential attackers ever new possibilities to attack a target.
“Robots do more now than they ever have, and some companies are moving forward with, not just the assembly line robots, but free-standing robots that can actually drive around factory floors. In that type of setting, you can imagine how dangerous this could be if a hacker gains access to those machines. At a minimum, they could cause harm to whatever products are being produced. If it’s a large enough robot, it could destroy parts or the assembly line. In a worst-case scenario, it could injure or cause death to the humans in the vicinity.” – Raheem Beyah (Professor at Georgia Tech’s School of Electrical and Computer Engineering)
HoneyBot is designed to look like a normal remote-controlled robot for anyone trying to access it remotely and then provide sensor data and motion information to the user. The difference, however, is that HoneyBot can give simulated answers to these commands without executing them in the real world.
For example, if an attacker tried to control the device into a production line, HoneyBot could send him an output indicating that he has done exactly that – while actually just remaining idle – but warning nearby personnel that he has been compromised. Once hackers have gained access to this bait, they also leave valuable information that can help companies further secure their networks.









