Cyber attacks: new dangers for IIoT and Smart Buildings
According to studies and surveys, although IT security on the Internet of Things is highly valued by most companies, many of them are still reluctant to invest in it. The ever-increasing number of cyber attacks proves the need for action.
In the coming week, from 1st to 5th April, the Hannover Messe Industrie will once again take place, where numerous manufacturers and suppliers will present new innovations and products for the industry 4.0.
Kaspersky Lab at the Hanover Fair Industry
However, representatives of the renowned security specialist Kaspersky Lab will also be present at the fair [Hall 12, Stand D45, (01)]. With excerpts from their Kaspersky Report for the second half of 2018, they want to draw increased attention to the greatest sources of danger for industrial computers – because so far, on average, only about half of all known vulnerabilities in industrial and IioT/IoT systems have been patched.
The greatest threat to these vulnerabilities is therefore the Internet (26 percent), removable media (8 percent) and incoming emails (5 percent).
“Most industrial computers are not infected by a targeted attack, but by widespread malware – by malware that inadvertently enters industrial systems via the Internet, removable media such as USB sticks or e-mails. The fact that the attacks are successful due to the lack of cyber-security hygiene of their own employees shows that a large part of the attacks can be prevented by training and sensitizing the workforce.” – Kirill Kruglov (Kaspersky Lab ICS CERT)
Point of attack industry 4.0
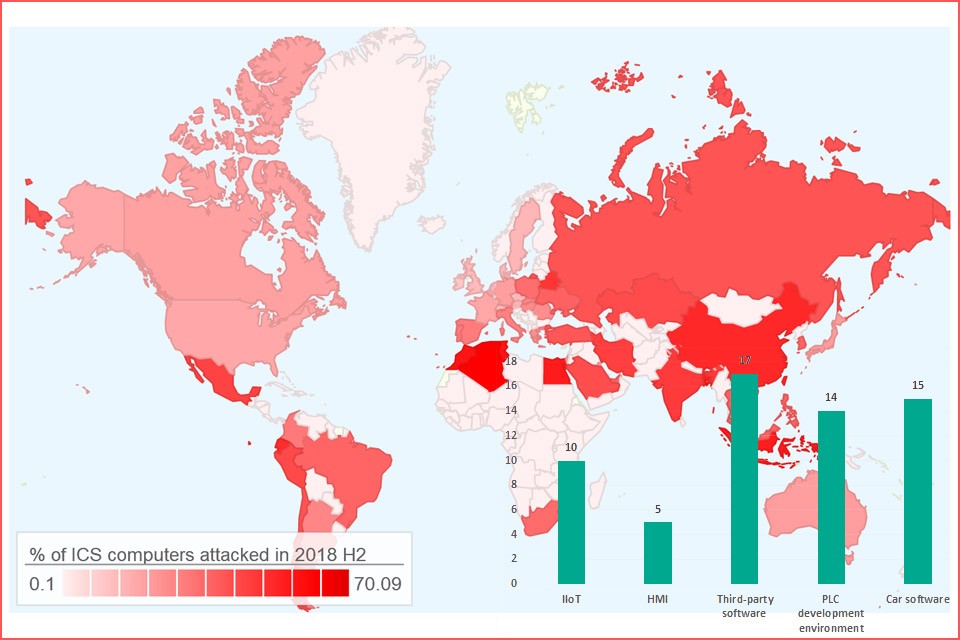
Kaspersky Lab experts examined industrial and IIoT/IoT systems for vulnerabilities. In 2018, 61 vulnerabilities were found, of which only 29 were fixed by the manufacturers. These were found in third-party software (17), vehicle software (15), PLC development environments (14), IIoT (10) and HMI (Human-Machine-Interface; 5).
Recommendations for more safety
Numerous measures for better protection against cyber attacks in the industrial IoT can be implemented cost-effectively; at most they require some working time. Recommended:
- Operating systems and application software on systems that are part of the company’s industrial network must be regularly updated, as is the case with the classic corporate network.
- Import security updates for PLC, RTU and network devices used in ICS networks.
- Limit network traffic to ports and protocols used on edge routers and within the organization’s OT networks.
- Check access control for ICS components in the enterprise industrial network and at its boundaries.
- Use a dedicated protection solution on ICS servers, workstations and HMIs such as Kaspersky Industrial CyberSecurity [2]. This solution includes network traffic monitoring, analysis and detection to protect OT and industrial infrastructure from random malware infections and dedicated industrial threats.
- Keep security solutions and technologies up to date and ensure that all vendor-recommended protection technologies are enabled.
- Train employees, partners and suppliers who have access to the network.
Smart Buildings as an attack target
In addition to Kaspersky Lab, Trend Micro (TM) recently also warned against cyber attacks on buildings and homes in the wake of the publication of their latest research results, because IoT automation platforms in smart buildings offer attackers new opportunities for physical and data-related threats.
In TM’s latest analysis, the “Cybersecurity Risks in Complex IoT Environments: Threats to Smart Homes, Buildings and Other Structures” report, Trend Micro warns of the potential consequences of the increasing use of automation platforms to chain multiple devices and create user-friendly intelligent applications. This would unintentionally create new and unpredictable targets that are difficult to control.
“IoT devices, their applications and the environments in which they are deployed have all quickly become more complex, but security is still not integrated into these devices. Today, personal and corporate data can pass through many routers, an IoT controller, multiple IoT protocols, and more in everyday work. This creates ideal conditions for criminals: Why attack a strong company when an employee’s smart home outside the company building is extremely vulnerable?” – Udo Schneider (Trend Micro)
TM’s researchers found that the biggest problem with automation rules in the structures described above is that they become more complex as more devices and functions are added. They are susceptible to logic errors and it becomes increasingly difficult to manage, track and debug functions – especially when there are functional overlaps between rules.
This results in a variety of new threats that are specifically relevant to complex IoT environments, such as the more than 6,200 Home Assistant servers that TM has been able to find through a simple Shodan search.
[“Shodan is a search engine that lets the user find specific types of computers (webcams, routers, servers, etc.) connected to the internet using a variety of filters. Some have also described it as a search engine of service banners, which are metadata that the server sends back to the client. This can be information about the server software, what options the service supports, a welcome message or anything else that the client can find out before interacting with the server.” Source: Wikipedia]
Attackers could use this security oversight to invade smart builds or re-program automation rules, steal hard-coded sensitive data including router logins, add new devices, infect devices with malware, or embed devices in botnets.
Trend Micro also recommends some measures to increase security against cyber attacks. Including:
- Update device firmware
- Activate password protection
- Change default settings
- No jailbreaks of devices or installations of non-verified third party applications
- Enable encryption in both hard drives and communication platforms
- Create regular backups of the IoT Automation Server configuration and automation rule files.
In addition, the choice of a qualified, renowned provider – high-quality hardware and software – brings more security with it than resorting to an inexpensive “China solution”.