Human vs. machine: Edge intelligence makes the IoT safer
The Internet of Things might not grow as quickly as predicted by some market researchers and analysts. In the long term, however, our lives will depend increasingly on connected technologies. The result of this development is that we will be more vulnerable. Despite this, the issue of security is often treated with negligence. But whoever wants to take the easy way out, pushes the residual rest on the “human factor”. We have to think further.
If a cyberattack occurs, usually those who are affected most are those that left their software and systems unattended and outdated. Security gaps are caused by neglected updates and poor or missing passwords. If systems then depend directly on each other, global failure can occur rapidly.
Up until now, online attacks were usually carried out by thousands of “captured” PC systems. Now, criminals are discovering the new possibilities of the Internet of Things: In addition to standard computers, millions of additional devices are being connected to the internet every year. As was the case before, carelessness regarding security issues, often performed by the manufacturers themselves, makes it an El Dorado for cybercriminals.
For example, a search for “camera” through the website www.shodan.io (a search engine specialized on IoT devices) results in almost 300,000 live IP addresses. Shodan usually also names the type of the connected device. If security issues or standard passwords of these devices are known, attackers can now easily gain access. Their goal is not to take a sneak peek into the homes of their users – that might be just secondary fun for online criminals – much more interesting is the ability to abuse these devices for large scale DDoS attacks on third party systems. The attackers of Mirai took a similar approach: They searched the network for devices that have been operated with default settings or without a firewall.
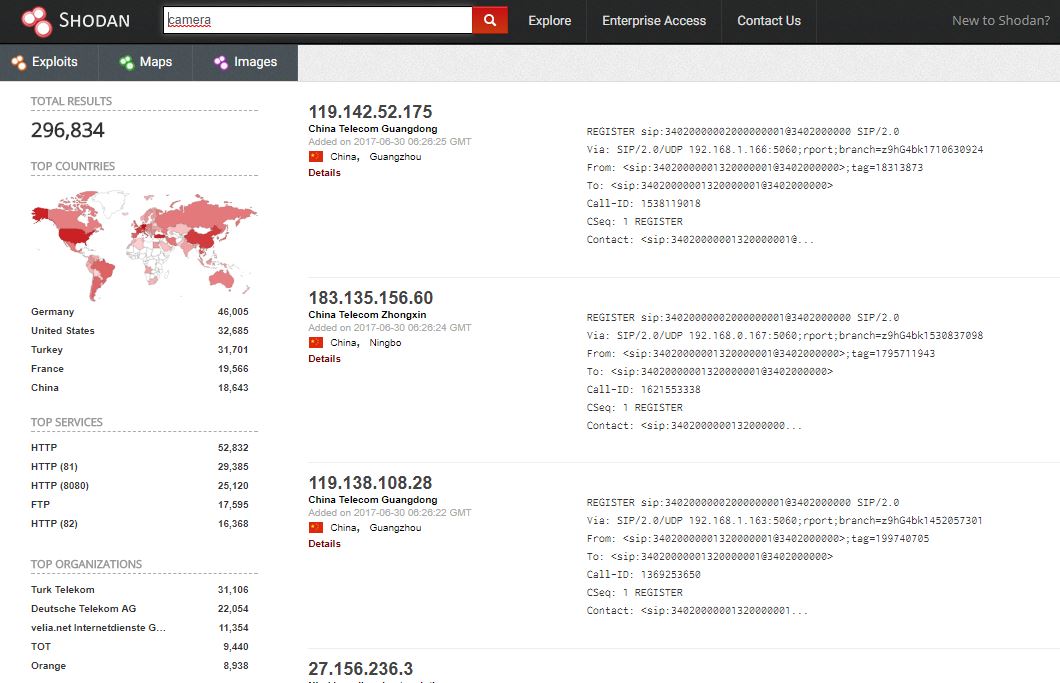
IoT Search Engine Shondan: Millions of IoT devices are already connected to the Internet, making it an El Dorado for cybercriminals
Weak link: human factor
It’s not always the devices that are to blame. The human factor can be a problem too. Namely whenever it is left up to the user to set a secure password or to decide whether to open an infected file. Every user has no doubt experienced this frustration when online services (or the admin in the company network) prescribe the structure of a password. Minimum length, upper and lower case, at least one special character. And best of all: Please invent a new one – every four weeks.
It’s annoying but it’s the result of widespread negligence. However, this compulsion might also have counterproductive consequences. For example, when just a single digit is attached to a standard password which is then simply “counted up” whenever an update is requested. Compulsive measures also affect the human memory: We become creative in avoiding complex rules.
But when it comes to the internet, we need high-security standards: starting with securing the access of end user devices, the authentication of new devices in an IoT environment, the type of encryption, up to the exchange of certificates amongst each other. Think of the madness, if one must manually enter secure passwords for every single device.
Manufacturers should design the installation process in such a way, that the devices are neither open by default nor accessible with easy to guess passwords. The task is to master the difficult balancing act between user friendliness and security.
Balance between costs and benefits
When implementing security mechanisms, it is always important to balance costs and benefits. A nosey neighbor, for example, can be blocked from the smart home system by using a good password.
Sometimes security gaps that experts have discovered on consumer products seem to be hypothetical: Recently, the German Chaos Computer Club criticized a weak spot in Samsung’s new smartphone flagship Galaxy S8. The built-in iris scanner for accessing the phone can be tricked. However, to achieve this, a photo has to be taken of the eye of the lawful owner in the smartphones “night mode”. If this photo is printed out and placed into a contact lens, the smartphone cannot distinguish this DIY “artificial eye” from the original. A security gap, no question, but nothing that can be done by an “occasional” data thief. Then again, for a high-profile politician or a bearer of secrets of a company, this product wouldn’t be suitable. For the rest of us though, it’s less of a concern.
Edge Intelligence: Decentralized IoT ecosystems bring more security
Attacks on individual devices are one thing, hijacking a complete IoT environment is something completely different. Conventional IoT installations usually have a major weakness: in almost all cases, the intelligence is located at a central point, either on a gateway or in the cloud. Anyone who gets access to it could take over complete control.
A decentralized “edge intelligence” approach, on the other hand, offers a smaller area of attack insolation. If the intelligence is transferred to the end devices, they can interact directly with each other. Only the data for monitoring or analysis are being transmitted for central processing. If a server, a gateway, or even the internet connection is now immobilized by an attack, a solution for example like an automatic building control system with its various intelligent sensors and actuators for climate or light control still remains functional.
This approach, known in the IoT world as “Edge Computing“, is where important processes already take place – at the edge of the network or near the actual end devices. In the industry, a shift away from centralized to decentralized solutions can be observed: In May, Microsoft announced its cloud platform “Edge” that aims to bring more intelligence closer to the devices.
In addition to increased security, there are further advantages: the response times are shorter, less data flow saves bandwidths and by the elimination of central entities, the complexities in IoT environments can be reduced. The latter results in lower engineering and maintenance costs.
Summarization
The average user cannot be transformed into an IT security expert. Costs and benefits cease to hold a meaningful balance. As a result, manufacturers will have to (and want to) make their products as “attack-proof” and at the same time as user-friendly as possible. A shift from centralized to decentralized solutions will additionally provide more security.









